Intensification of Information Security | ACER ESG
Corporate information security management strategy and framework

Management of Information Security Effectiveness
The company continues to address information security risks by conducting third-party assessments and implementing necessary corrections to ensure compliance with industry standards for information security protection mechanisms.
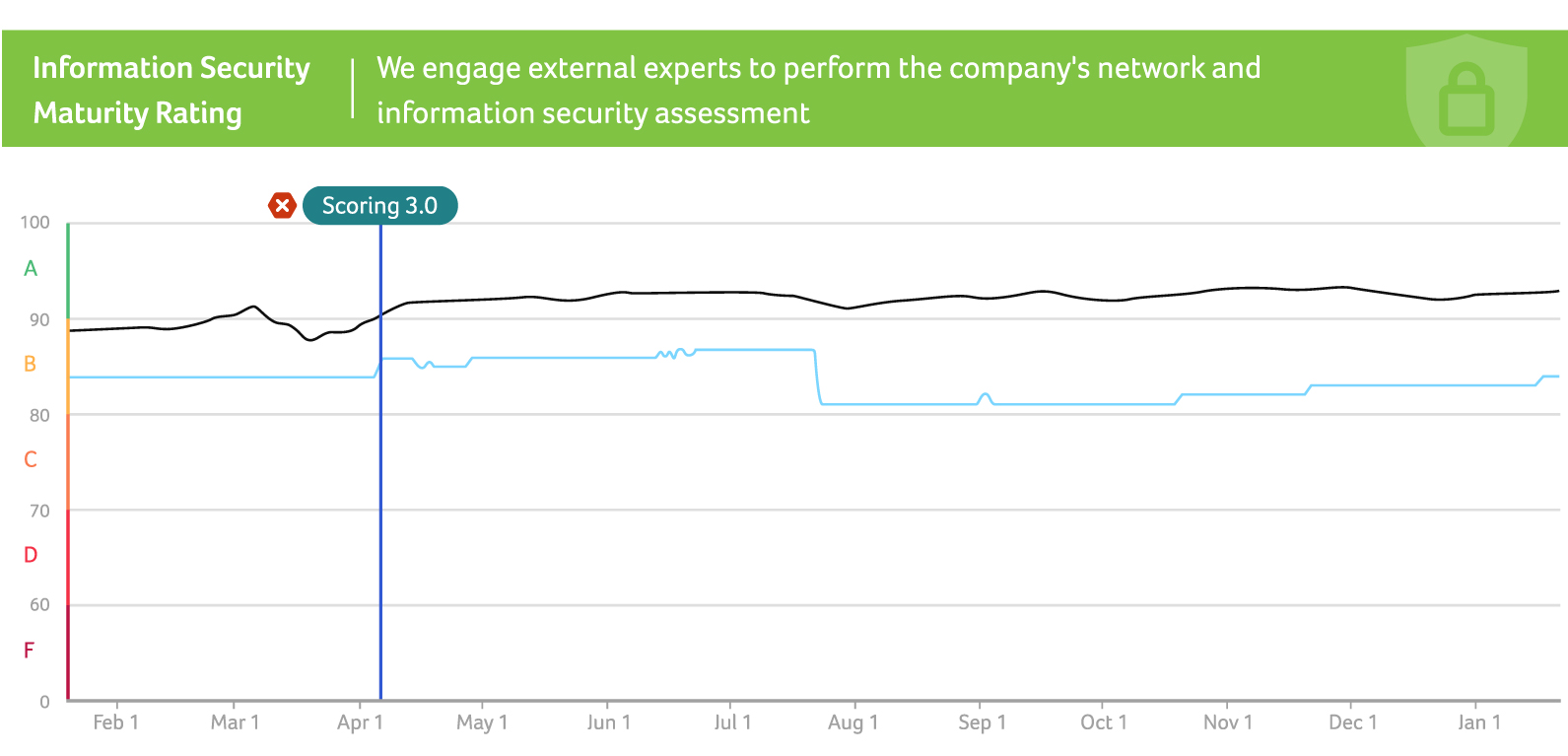
- The industry average is shown as the blue curve, with a score of approximately 83 and a maturity rating of B.
- Acer's data is represented by the black curve, consistently above the industry average throughout the year. Since early April, Acer has maintained a score above 90 and sustained a maturity rating at level A.
Investments in the cyber security management
Performance of Information Security Implementation in 2024:
01 | Policy
Headquarters Adds/Revises 18 ISMS Information Security Management Directions and Regulations
Headquarters Adds/Revises 5 CSF Information Security Regulations
02 | Certification
- The headquarters successfully completed the initial verification of ISO/IEC 27001:2013 in 2019
- The headquarters successfully completed the reverification
of ISO/IEC 27001:2013 in 2022 - Headquarters was re-certified for ISO/IEC 27001:2013 in
2023 - EMEA IT completed the initial verification for ISO/IEC
27001:2013 in 2023 - The headquarters was re-certified for ISO/IEC 27001:2013 in 2023
03 | Promotion
10 videos
Produce a promotional video and conduct 26 informational seminars to convey essential regulations and precautions regarding information security
595 persons
A total of 595 new employees completed the information security briefing during the new employee orientation
10 Announcements
A total of 10 Information Security announcements were made to convey important regulations and precautions regarding information security
04 | Risk Control
5,728 persons
5,728 employees have completed the annual online information security education and training course
2 social engineering drills
Conducted 2 email social engineering drills, involving over 7,000 participant
11 penetration tests
Conduct one annual penetration test and 11 project-based penetration tests, inspecting over 100 targets
1 web vulnerability scans
Conducted 1 web vulnerability scans, checking a total of 311 websites
4 OS vulnerability scans
Conducted 4 OS vulnerability scans, examining over 8,000 vulnerabilities
Cyber Security Risks and Response Measures
Acer has established comprehensive information security protection measures for our network and computers, but this cannot guarantee that the computer systems that support our business operation will be completely free from cyber attacks that could cause the loss of important Acer data. Malicious hackers or cyber attacks motivated by geopolitics may introduce viruses, destructive software, or ransomware to the Company’s network systems, interfering with Acer’s operations.

Acer has faced an attack from ransomware from a member of our staff accidentally clicking on a phishing mail, and we may face similar attacks in the future. To prevent damage from such attacks, Acer implements related corrective actions and continually works to optimize our practices. For instance, we have reduced the chances for phishing emails to make it to inboxes; strengthened firewall controls and Internet access to prevent malware from expanding to other zones; implemented multi-layer management of privileged accounts to prevent them from being hacked; introduced leading solutions for compliance auditing; imported new techniques to detect and handle malware; and routinely executed vulnerability scans & fixes and test staff awareness.
The future focus of our information security
 | No leakage of customers’ data.With multi-layer protection, hackers cannot access customer data even if Acer is under attack from ransomware. |
 | Enhance the comprehensive information security and monitoring mechanismIn doing so, we can make cyber attacks more difficult and thus lower the inclination of hackers to attempt them. Acer deploys endpoint detection and responsive software to ensure the visibility of any abnormal behaviors. |
 | Segregate internal systemsAdopt a zero trust framework in the data centers of both regional offices and headquarters and enhance business continuity drills for information systems, mitigating the impact of attacks and enabling systems to recover within a tolerable time. |










